
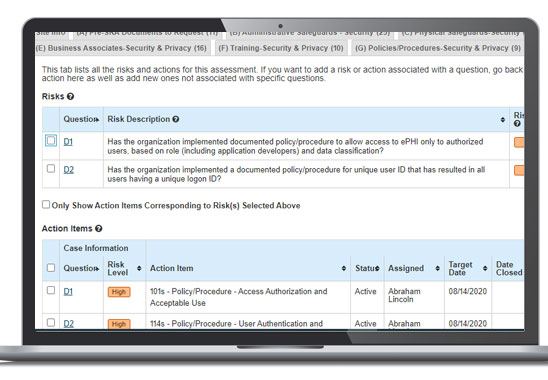
Why Do a Security Risk Assessment?
A Security Risk Assessment (SRA) is the foundation of a healthcare organization’s data protection strategy — and a key requirement for HIPAA and HITECH compliance. It’s a structured evaluation of how your organization safeguards electronic protected health information (ePHI), identifies vulnerabilities, and measures the likelihood and potential impact of security threats. In healthcare, where technology and patient care are deeply intertwined, an SRA isn’t just about compliance — it’s about protecting patients, maintaining trust, and ensuring operational resilience.
At Genzeon, we help healthcare organizations navigate the complex intersection of technology, security, and regulation. Our expert-led SRA process delivers clear insights and actionable recommendations tailored to your systems, workflows, and risk profile. We don’t just identify gaps — we help you close them, strengthen your defenses, and build a culture of continuous security awareness.
HOW WE WORK
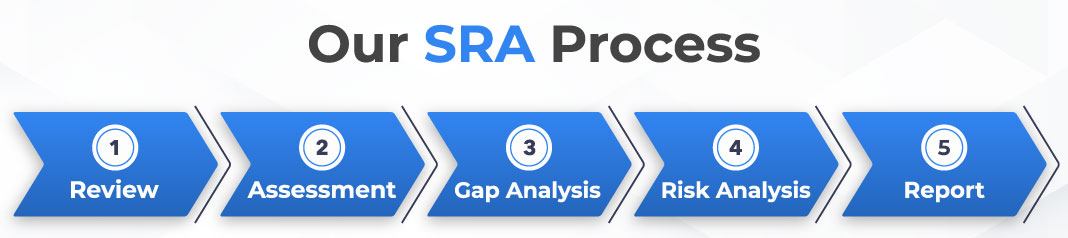
Security Risk Assessment Process
Our comprehensive security risk assessment (SRA) consists of a number of steps and significant documentation review. Below outlines the basic progression within an SRA.
- Pre-assessment Documentation Collection & Review
- Current Stat Assessment
- Security Risk Assessment
- Virtual Site Assessment
- Summarize Findings, Risks, and Gaps
- Provide Remediation Options and Attestation (if required)
SRA COVERAGE
Scope of CPS Security Risk Assessments
These areas listed below are examples of what CPS covers; however, this is not an exhaustive list. We are continually reviewing and revising the SRA content based on evolving standards and regulations.

- Email & Web Security
- End Point Detection & Response (EDR)
- Account & Access Mgmt (IAM)
- Data Protection & Loss Prevention
- Asset Management
- Network Security
- Patch & Vulnerability Management
- Incident Mgmt, Remediation, Sanctions
- Contingency Plan, Secured, Verified Backups
- Workforce Security & Cybersecurity Training
- Auditing & Monitoring
- Vendor & Supply Chain Management
- Info Security Governance, Policy/Procedure
- Physical Info Security Safeguards
- Medical Device Security
- Emerging Technologies (AI, IoMT, Quantum Computing)
REPORTS & FINDINGS
What You'll Get From Your SRA
At the end of the SRA process you will receive a HIPAA/405(d) Security Risk Assessment report, either in a downloadable format, or in the CompliancePro Solutions application. Our team will then walk you through the highlights of that report, including risks and recommended remediation actions.
In future years, if you are working within the CPS platform, many of the answers from the previous year can be copied over to speed up the process before updating any changes within your organization.
Secure Your Company's Data
Talk to our security risk experts to learn more how Genzeon can help.
DOCUMENTATION
Examples of Useful Pre-Assessment Documentation
These are representative of the types of documentation that are helpful in completing an SRA. Ideally, they should be obtained prior to the interviews to streamline the assessment process.
Security Specific Policies & Procedures
- Security Risk Analysis documentation
- Security Compliance Program (Plan)
- Security Policy/procedure
- Security Officer Job Description
- Security Training documentation
Other Policies & Procedures
- Social Media policy/procedure
- Org chart identifying security and privacy officers
- Facility physical security plan
- Change control policy/procedure
- Secure Software Development Life Cycle (SSDLC) policy/procedure
- BA Privacy & Security Compliance Questionnaire
- HR – Onboarding and offboarding policy/procedures
Asset Inventories
- Asset Inventory-hardware
- Asset inventory- sensitive data
- Asset inventory-medical devices
Proactive/Reactive Measures
- Penetration testing policy/procedure
- Vulnerability Scan policy/procedure
- Incident Response walkthrough/simulations
- Business Continuity Disaster recovery Plan
- Security Incident Mgmt/Incident Response Plan
- Emergency Mode Operation
Data/Network Specific
- Data flow diagrams ePHI
- Pre-production / test environment policy/procedure
- Remote Access / work from home policy/procedure
- Data backup and restore policy and procedure
- Network Diagrams – internal and external connectivity showing deployed security controls
- Data classification and security policy/procedures
- Facility maintenance and security procedures
3rd Party & Vendors
- Third party software review
- Vendor Supply chain review
- List of cloud service providers with sensitive data
- Hardware pre-procurement SRAs
RELEVANT INSIGHTS





